


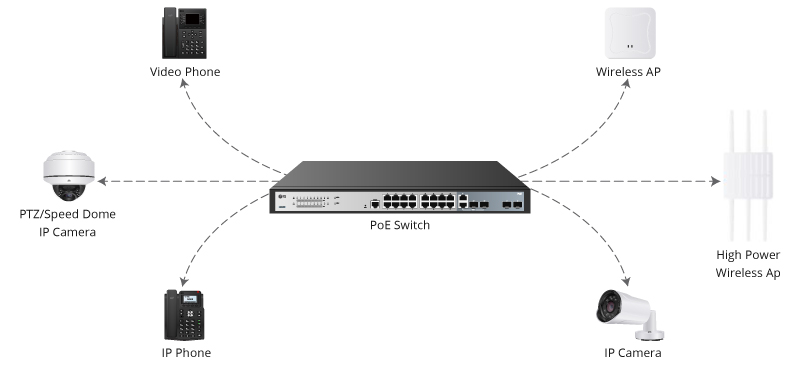
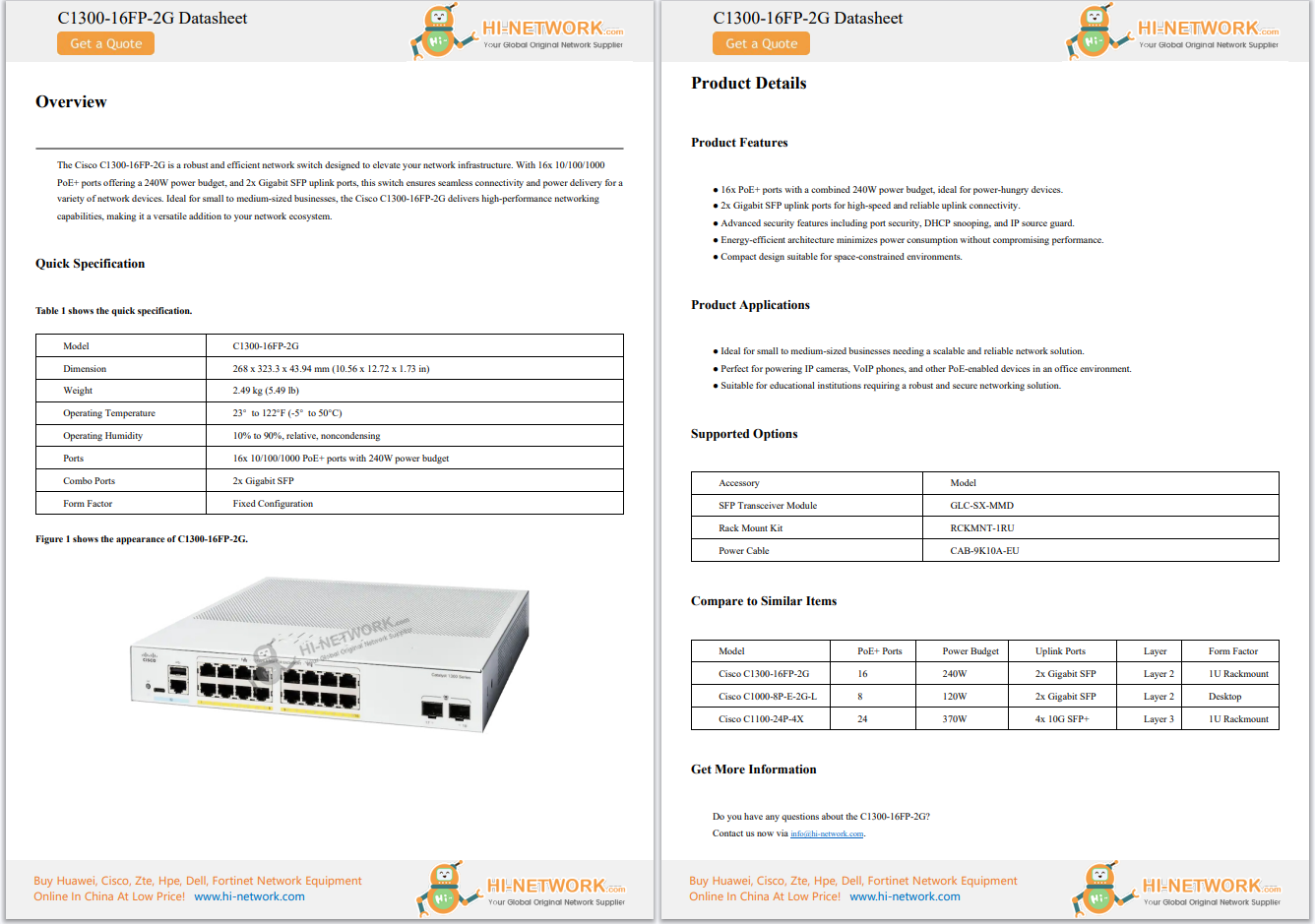






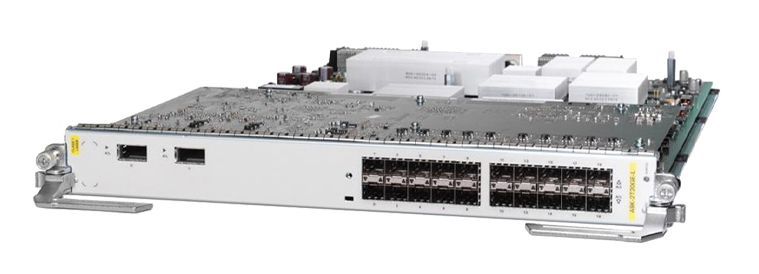






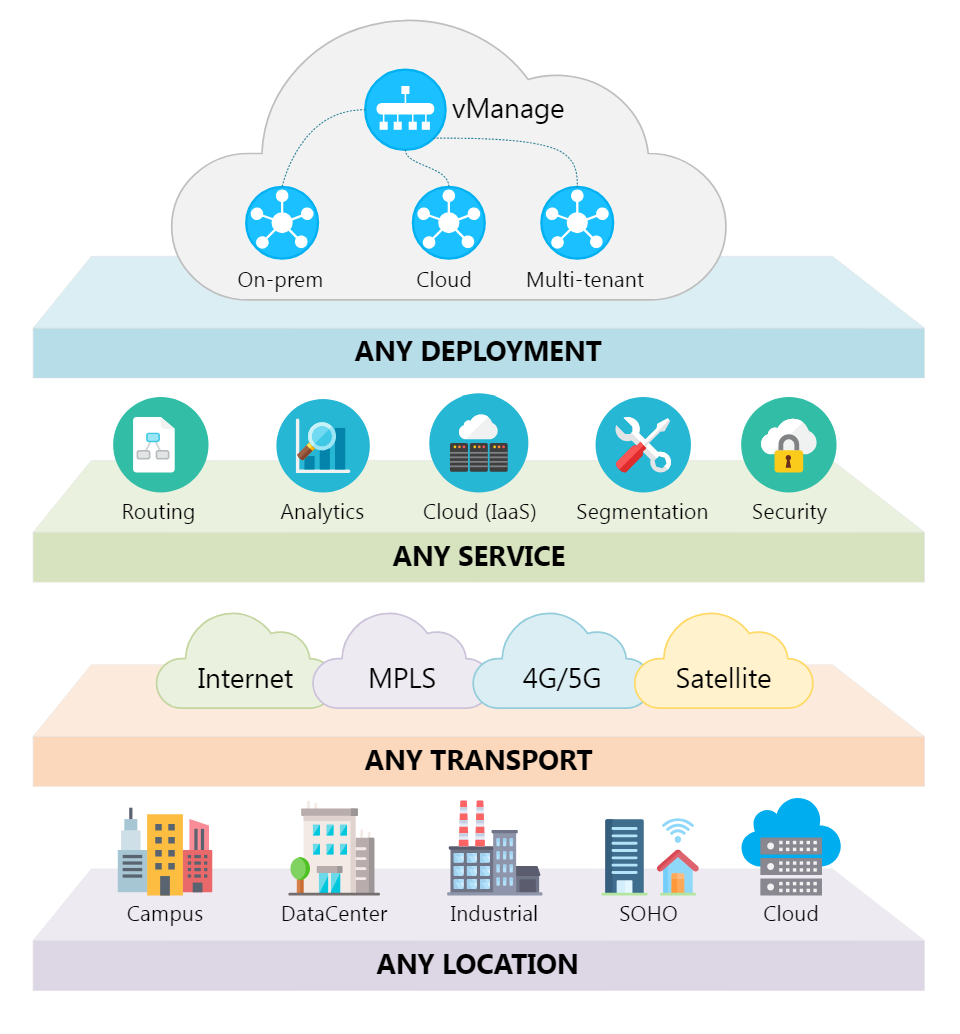
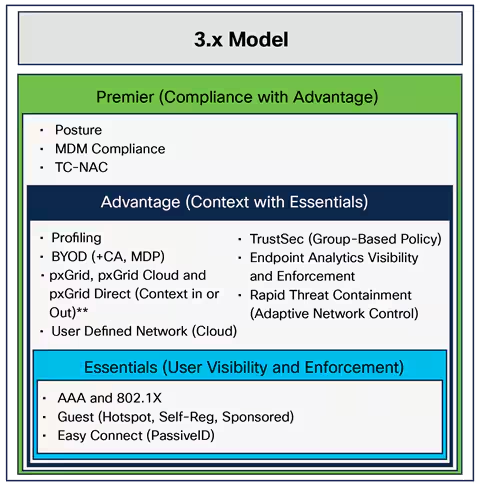


Day 2 of Educause 2013 has been both information-filled and somewhat fascinating. During the general session this morning, author and renowned game designer, Jane McGonigal, shared some intriguing facts about the power of gaming i...

When your incident response team gets access to a new log data source, chances are that the events may not only contain an entirely different type of data, but may also be formatted differently than any log data source you already...

There are two ways to write this blog. One is all positive, happy and humorous. The other is to be real. I've wrote both versions. I like the happy one better. I had some funny, "You know you're fat when..." Foxworthy-isc quips......

DNS is like the town gossip of the network infrastructure. Computers and apps ask DNS questions and you can ask DNS who has been asking to resolve malware domains. When internal trusted systems are using DNS to resolve the names o...

Every Friday, we'll highlight the most important Cisco partner news and stories of the week, as well as point you to important, Cisco-related partner content you may have missed along the way. Here's what you might have missed thi...

Dude, where's my IP? I love to check in on social networks like Foursquare and Google+. Most of the time, there's no point to it, but it's fun to see what friends and colleagues are up to or discover new local haunts. Despite the ...

Guest post by Dennis Clark, Senior Solutions Marketing Manager -Microsoft Applications, NetApp We are here in Charlotte this week with our Cisco friends, with the opportunity to talk with all sorts of like-minded Microsoft SQL Ser...

Intel estimates1that one-third of the servers in production are more than four years old. At first, one might think that it is great to get this much service out of a capital investment, but the operational costs to run these outd...

Cryptography is critical to secure, trustworthy communications. Recent questions within the tech industry have created entirely new discussions about the cryptography underpinning our communications infrastructure. While some in t...

Now when I'm talking about safekeeping a mobile device, I'm not saying don't use your Kindle by the pool or let your toddler play on the iPad while eating ice cream. These are dangerous things to be doing with a gadget, but today ...

This is the latest in a series of posts featuring partner success stories where partners share how they're helping customers achieve their goals by using Cisco technology. This week we're pleased to feature Scott Alexander, Presid...

Recently, I was chatting with Hugo Vliegen, Director of Technical marketing, Enterprise Networks, and he was telling me all of the questions he had been getting from customers about the Cisco UCS E-Series. Questions such as:...