


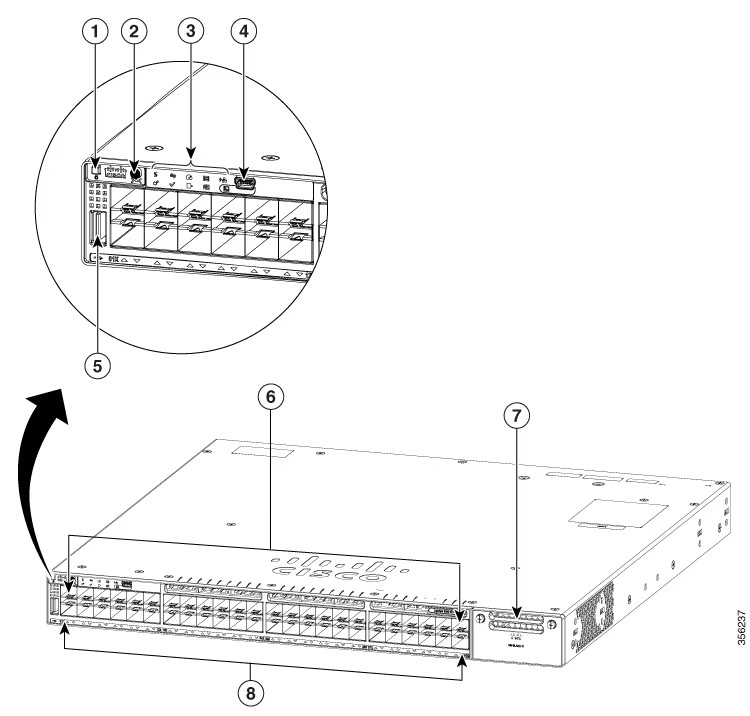













Your business invests in all the latest security technologies. You run training. You meet your compliance requirements for scans and tests. You can stand up in front of the board and say with confidence "we've got this covered."
But are you as prepared as you think?
New research from ESG sheds new light on threat readiness. Read on for four key findings you can't afford to ignore.
Want the full story? Join us for a webinar on Dec. 4, 2019. You can register here.
According to ESG's latest research on incident readiness trends, 92 percent of IT security practitioners surveyed feel "good to excellent" about their ability to quickly detect and respond to cyber incidents. On average, they scored themselves eight out of 10 that they could completely mitigate a destructive attack.
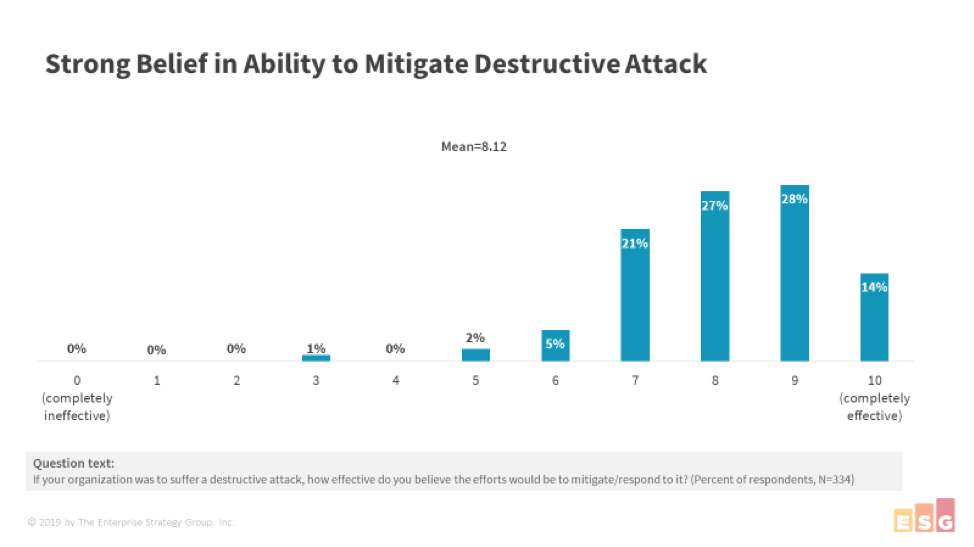
But all the evidence tells us that the reality is very different. In the same survey, 35 percent of respondents said they had suffered a destructive attack, and of those, 41 percent indicated that it took a month or more to detect the attack.
We know that the ability to prevent, detect and respond quickly to security incidents is a trained behavior - it has to be practiced.
ESG's research specifically surveyed security professionals who had engaged in threat-readiness activities within the last 18 months, asking about a whole range of activities, from pen testing, tabletop exercises, red teaming and more.
"From ESG's data, and our own experiences in the field, we see a degree of overconfidence about threat readiness," Sean Mason, director of Talos Incident Response, said. "Being blunt, that's dangerous. As a CIO or CISO responsible for the results of incident response efforts, it's incumbent on you to paint a real picture of risk for your board, without sugarcoating.
The fact is, security is hard work, threats are always changing, and perfect defense is impossible - but the only thing to do is to keep striving for continuous improvement and avoid complacency. Keep plans up to date. Test them. Train hard, and don't stop."
Nine out of 10 organizations surveyed have performed incident readiness exercises in-house over the last 12-18 months. Of those respondents who have used internal teams and third-party service providers to perform incident readiness exercises, 58 percent say they perform the majority of their incident readiness exercises in-house. And that trend isn't going away. More than half say they'll hire or train more security analysts over the next 12-18 months to improve incident readiness.
This is hard to reconcile with the harsh reality of the IT talent gap. According to ESG's 2019 Technology Spending Intentions Survey, cybersecurity remains the discipline most acutely affected by skills shortages.
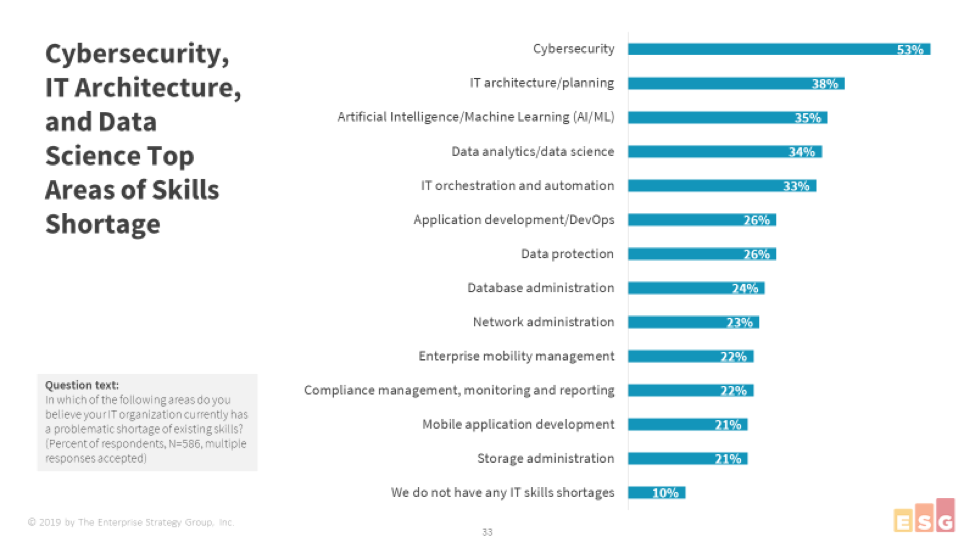
"The truth is that simply due to market dynamics, most in-house IT teams struggle to recruit, let alone retain, the very best talent," Mason said.
Whether a CIO sticks with a recruitment strategy or chooses to source expertise from specialist vendors, budget becomes the sticking point.
"Security teams consistently cite lack of budget as one of the biggest weaknesses in their threat readiness," says Christina Richmond, principal analyst at ESG. "In fact, it's often that only after suffering an attack does the business assign more budget to incident readiness."
ESG found that less than a third of security teams have C-level involvement in all incident readiness activities.
"In our experience, organizations with the strongest security practices and the healthiest budgets are those where there is C-level engagement in the strategy. I've been lucky enough to experience it in my career, but it's all too rare," Mason said. "The sad truth is that it's often only a breach that gets the attention of the CEO - and no CIO or CISO wants to have that conversation."
The key to winning board-level sponsorship and budget for security is the same as for any business initiative: prove your value with data. That's the language your CEO speaks.
Only 29 percent of survey respondents said they are able to regularly report metrics aligned to business, risk management and C-level objectives.
The numbers that talk the loudest?
"Look for the financial impact of security success: benchmark fines and legal settlements from breaches in your industry," Mason said. "Estimate the impact on customer trust and brand goodwill, the cost of supply-chain downtime and employee productivity."
ESG data indicates that only 29 percent of organizations are actually able to measure the financial impact of an incident today - there's work still to do. But it's important work. These measures will speak louder to a non-technical audience than operational metrics. And when you do use operational metrics, such as time to respond, put them in context with industry benchmarks to make them more meaningful.

Security leaders have a wide range of tools in their incident-readiness kit, ranging from strategic maturity assessments to automated scans, tabletop exercises, penetration testing, threat hunting and more.
"Our research found the use of various incident response activities in the last 18 months was unbalanced," says Richmond. "Assessments made up three of the top five activities most commonly performed; while actual practice exercises made up all of the bottom five."

"In truth, you can't say that you have a plan until you've tested it to see if it works," says Mason. "That's closing the loop from assessment, to plan development, to testing and back around to assessment. Running exercises and simulations is critical for ensuring that teams can react calmly and decisively when an incident happens."
Discover the full findings from ESG's research and pose your questions to Sean Mason and Christina Richmond on our free webinar on Dec. 4 2019, 9 a.m. PST. Register now.
Find out how Cisco CX can help you improve your threat readiness.
 Tags quentes :
#Segurança
Cisco Talos
Talos
incident response
webinar
Talos Incident Response
Talos IR
Tags quentes :
#Segurança
Cisco Talos
Talos
incident response
webinar
Talos Incident Response
Talos IR