















Cisco is pleased to announce a new series ofForensic Investigation Procedures for First Respondersguides that will help customers and partners triage Cisco products that are suspected of being tampered with or compromised. These guides provide step-by-step instructions for collecting information that first responders can use for forensic analysis for several different platforms, including devices that run Cisco IOS and IOS XE Software, and devices that run Cisco ASA or Firepower Threat Defense (FTD) Software.
These new documents are available on the Cisco.com Security Portal under Tactical Resources.
The following is a summary of the documents released thus far, along with a brief description of each one.
Cisco ASA Forensic Investigation Procedures for First Responders
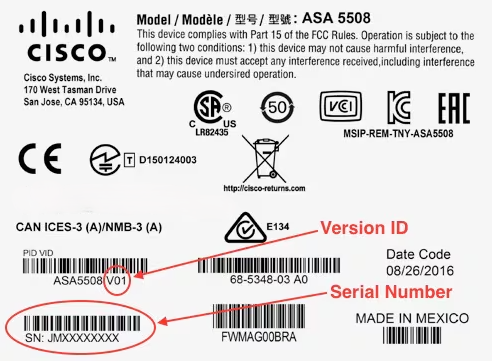
This document provides guidance for collecting forensic evidence from the Cisco ASA 5500-X series of devices when compromise or tampering is suspected. It outlines several procedures for collecting platform configuration and run time state, examining system image hashes for inconsistencies, verifying the system and running images for proper signing characteristics, checking the ROM monitor configuration for signs of remote image loading, and procedures for obtaining both a core file and the memory text segment from an ASA platform.
The document also includes a procedure for checking the integrity of the webvpn configuration for ASA deployments implementing SSL VPN.
Cisco FTD Forensic Investigation Procedures for First Responders
This document provides steps for collecting forensic information from Cisco ASA 5500-X devices running Firepower Threat Defense (FTD) Software when compromise or tampering is suspected. This document contains procedures for collecting platform configuration and run time state, examining system image hashes for inconsistencies, verifying proper signing characteristics of FTD system and running images, retrieving and verifying the memory text segment, generating and retrieving both crashinfo and core files, and examining the ROM monitor settings for remote system image loading.
Cisco IOS Software Forensic Investigation Procedures for First Responders
This document provides guidance for collecting evidence from Cisco IOS devices when compromise or tampering is suspected and includes procedures for collecting platform configuration and run time state, examining system image hashes for inconsistencies, examining the ROM monitor region for an upgraded image, and obtaining both a core dump of the running IOS image and the contents of the memory text region.
The document also includes a procedure that provides an alternate method of image analysis if a core dump cannot be performed on a platform that is performing mission-critical traffic forwarding.
Cisco IOS XE Software Forensic Investigation Procedures for First Responders
This document provides guidance for collecting evidence from Cisco IOS XE devices when compromise or tampering is suspected and includes procedures for collecting platform configuration and run time state, examining system image hashes for inconsistencies, verifying the integrity and signing characteristics of system and running images, and exporting the text memory segment to verify the run time integrity of the IOSd process.
 Tags quentes :
Segurança
Segurança cibernética
Ios
Destaque
ASA
first responder
ftd
Tags quentes :
Segurança
Segurança cibernética
Ios
Destaque
ASA
first responder
ftd