































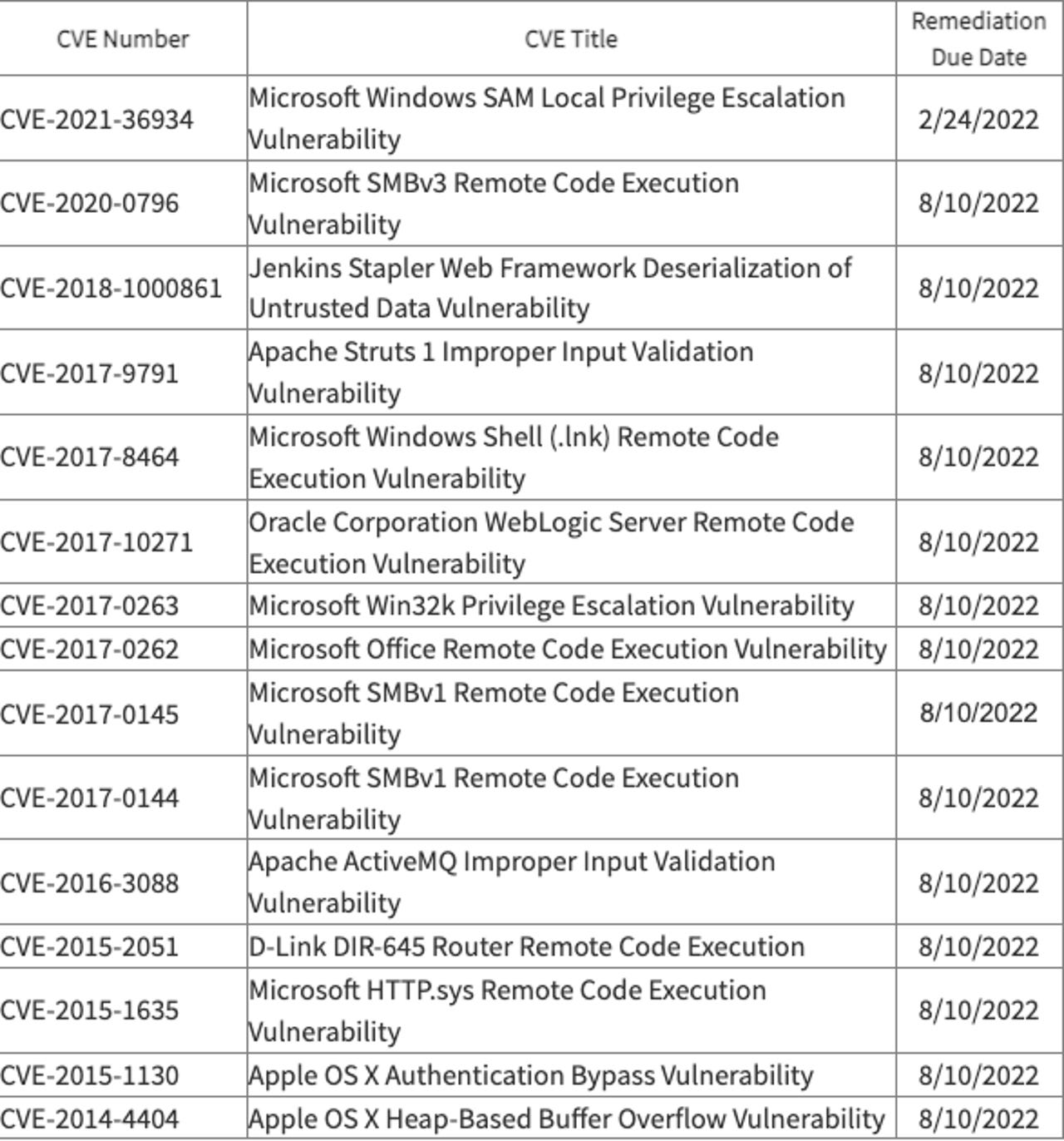
The US Cybersecurity and Infrastructure Security Agency (CISA) updated its catalog of known exploited vulnerabilities this week, adding 15 vulnerabilities based on evidence that threat actors are actively exploiting them.
The list includes a Microsoft Windows SAM local privilege escalation vulnerability with a remediation date set for February 24.
Vulcan Cyber engineer Mike Parkin said the vulnerability -- CVE-2021-36934 -- was patched in August 2021 shortly after it was disclosed.
"It is a local vulnerability, which reduces the risk of attack and gives more time to deploy the patch. CISA set the due date for Federal organizations who take direction from them, and that date is based on their own risk criteria," Parkin said. "With Microsoft releasing the fix 5 months ago, and given the relative threat, it is reasonable for them to set late February as the deadline."
The rest of the list covers a range of Microsoft, Apache, Apple, and Jenkins vulnerabilities with remediation dates of August 10.
While some experts questioned CISA's new additions to the list, Netenrich's John Bambenek explained that anything that provides a straightforward path to elevated privileges and is being exploited by the kind of threat actors CISA is concerned about needs to be remediated immediately.
 CISA
CISA Pravin Madhani, CEO of K2 Cyber Security, noted that more than half of the vulnerabilities are classified as remote code execution (RCE) vulnerabilities.
"RCE is one of the most dangerous types of vulnerabilities as it gives the attacker the ability to run almost any code on the hacked site. RCE, and other flaws such as XSS (Cross Site Scripting), have long been included on the OWASP Top 10 list, so why aren't companies better equipped to protect against these attacks?" Madhani asked.
Viakoo CEO Bud Broomhead said he believes cybercriminals are using older vulnerabilities in exploits against new device targets, specifically IoT devices.
As an example, Broomhead mentioned vulnerabilities that enable man-in-the-middle (MitM) attacks.
"Virtually all IT systems are protected against this threat, but IoT systems often are not, leading threat actors to revisit these older vulnerabilities knowing that network-connected IoT devices can be exploited through them," Broomhead said.
"This would lead to a vulnerability discovered years ago being added recently to the CISA catalogue. With close to 170,000 known vulnerabilities priority should be given to the ones that are causing real damage right now, not ones that in theory could cause damage."
 Tags quentes :
Tecnologia
Segurança
Tags quentes :
Tecnologia
Segurança