































Vulnerabilities that permit remote network attacks against ubiquitous software components are the nightmares of security professionals. On 24 September the presence of a new vulnerability, CVE-2014-6271 in Bash shell allowing remote code execution was disclosed.
The Bash shell is commonly included in many Linux distributions to allow remote users to interact with the system after logging in. As part of its functionality, Bash allows for environment variables that are commonly used to hold values describing the set-up of the shell for easy access by a user or software. Bash also contains limited programming functionality allowing the creation of functions that can be called to execute instructions. The vulnerability occurs during the initiation of a Bash shell for a user, when the environment variables are first read. If the environment variables contain functions then the code contained within the function will be executed. The danger is that in some circumstances the Bash shell environment variables may be set across a privilege boundary allowing a system or user with low privileges to execute arbitrary code.
The vulnerability affects Bash versions up to, and including 4.3. This affects many implementations of Linux, and may also concern electronic devices that include Bash to provide scripting functionality.
Redhat has provided proof of concept code that can be used to check if a system isvulnerable. After logging in to a Bash shell, enter:
env x='() { :;}; echo vulnerable' bash -c "echothis is a test"
A vulnerable system will display:
vulnerable
this is a test
A Metasploit module is available to test for the vulnerability. Although this provides network teams with the means to check if systems are vulnerable, potentially it also provides attackers with the resources to discover and exploit vulnerable systems first.
We have observed exploitation of the vulnerability in the wild. We have indications that at least some of this activity is due to an automated malicious attack seeking to install DDoS tools on affected systems. However due to the nature of this vulnerability almost any tool or malware sample can be downloaded and executed.
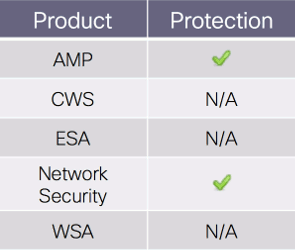
The best way to block this threat is using Network AMP or Network Security protection of IPS and NGFW. They have up-to-date signatures and will block this threat. The following signatures cover this threat:
Sourcefire: 31975-31978,31985
Cisco: 4689-0, 4689-1,4689-2,4689-3
The Cisco Product Security Incident Response Team (PSIRT) is currently investigating if any Cisco products are affected by this vulnerability. For the latest information, please see the Cisco Event Response: GNU Bash Environment Variable Command Injection Vulnerability.
 Tags quentes :
#Segurança
Cisco Talos
Talos
malware
worm
bash
shell shock
CVE-2014-6271
Tags quentes :
#Segurança
Cisco Talos
Talos
malware
worm
bash
shell shock
CVE-2014-6271